Fake Flash Player Malware Targets Android Phone Users
Cybercriminals are always on the lookout to make a fast buck from unsuspecting marks. Web sites that require Flash Player to be viewed properly often show a prompt to install the plug-in. However, this should not be accepted, as it may not be what it seems. Instead, the plug-in should always be obtained from official sources, such as the Adobe website itself.
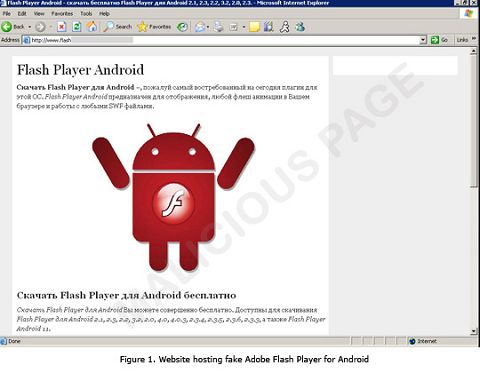
Trend Micro has discovered an infected website hosted on a Russian domain that offers to install Flash Player, claiming it to be compatible with all Android versions to help lure people in. However, it instead links to another URL to download a malicious .apk file which contains a malware-laced version of the Flash Player plug-in that Trend Micro has called ANDROIDOS_BOXER.A. This malware rips off the user by sending texts to premium numbers without the user’s permission, which can cost the victim around $10 a pop.
The infographic below shows a snapshot of Android threats. Click here to display a larger version of it – there’s no malware payload I promise you!

Upon further investigation, we have seen a bunch of URLs that are hosted on the same IP as this particular website. Based on the naming alone used in these URLs, it appears that Android is a favorite target for cybercriminals behind this scheme.

Comments are closed.