Microsoft Windows Exploit Allows Elevated Command Prompt Access At Login
It seems an unpatched exploit in Microsoft’s Windows 7, Windows 8 consumer preview and Windows Server 2008 R2 operating systems could become a serious issue. The exploit operates by changing a simple registry entry which changes the function of sticky keys to instead launch an elevated command prompt. While the exploit has been documented for sometime, Microsoft has yet to plug the security hole and it could spell disaster for companies. The hack itself is easy enough, anyone can do it by simply entering a few lines into a command prompt which then enables a user to return later and simply hit the shift key five times to access the elevated command prompt. Through these actions, an employee that has been fired, for instance, can access a workstation and steal confidential or important files and then delete them. More alarming is the fact that the hack is nearly undetectable unless checking the registry itself for changes and even works via remote access. So far, Microsoft has yet to release a statement on the exploit, hopefully it gets fixed sooner rather then later. For more info on exploit check the source.
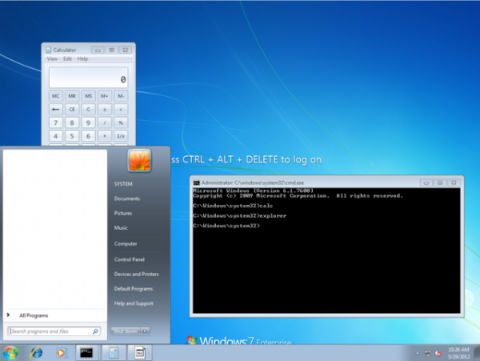
Depending on how fast you can type, this could easily be done in less than a minute. Once entered, a user can return to the workstation at a later date and launch the same high level command prompt at the login screen by pressing the Shift key five times. This usually activates sticky keys but the above code changes its function to launch the command prompt instead.

Comments are closed.