TrueCrypt Is Not Secure According To Own Developers Who Pull Plug

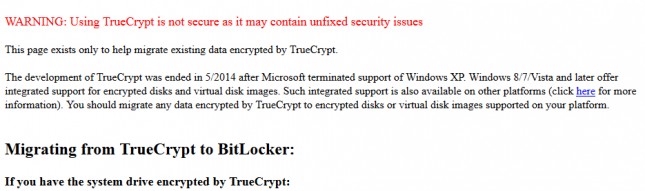
The homepage for TrueCrypt was changed Wednesday and redirected to the Sourceforge project page where there are directions on how to migrate data encrypted over to Bitlocker. The page also has an ominous warning about the software that reads “Using TrueCrypt is not secure as it may contain unfixed security issues.” “This page exists only to help migrate existing data encrypted by TrueCrypt.” The anonymous developers responsible for building and maintaining TrueCrypt have apparently thrown in the towel.
The site continued: “The development of TrueCrypt was ended in 5/2014 after Microsoft terminated support of Windows XP,” it read. “Windows 8/7/Vista and later offer integrated support for encrypted disks and virtual disk images. Such integrated support is also available on other platforms (click here for more information). You should migrate any data encrypted by TrueCrypt to encrypted disks or virtual disk images supported on your platform.”
The announcement is confusing because the developers link Truecrypt’s demise to Microsoft’s decision to cease supporting Windows XP, though no one seems to have a theory about how these two facts relate to one another.
Some believe that this is all due to the successful crowdfunded security audit of the open source file and disk encryption software package used by people all over the world. The unique effort to crowdsource a security audit of the TrueCrypt open source encryption was launched by two U.S. based researchers in response to concerns that the National Security Agency may have tampered TrueCrypt. According to the anonymous group that developed the software, there have around 30 million downloads of TrueCrypt. If TrueCrypt has a backdoor, it would impact many people around the world. Phase I of the audit was completed last month (read the full report here) and 11 vulnerabilities were found in Truecrypt’s bootloader, all rated Low to Medium severity. Phase II of the audit is currently taking place and is a formal cryptanalysis, as well as examine the OSX and Linux ports. Could the audit of the crypto have made the developers call it quits or has the site been hacked? Phase II was to be completed by the end of summer. The Register is reporting that the most recent version of TrueCrypt appears compromised.
It might be time to stay away from TrueCrypt as it doesn’t sound like anyone knows what is going on!
